Azure Multi-Factor Authentication - Part 1: Domain Users
This week, our guest blogger, Andrew Hinkle, presents a two-part series on how to use Multi-Factor Authentication in Azure and introduces a presenter for DogFoodCon.

DogFoodCon 2019 is October 3rd – 4th. Chris Lee and James Hopkins will be presenting [Office 365] Establishing the Baseline Security for Microsoft 365. I interviewed Chris Lee regarding their presentation and have included a summary at the end of this article.
Businesses with sensitive information prevent most attempts to hack into an account via a username and password by introducing Multi-Factor Authentication. The typical forms of authentication methods are a phone call, a text message, a notification in an authenticator app, or a verification code from an authenticator or hardware. I've use all of these methods to date. If you're a gamer like me you'll recognize the Steam Guard Mobile Authenticator and Blizzard Authenticator. Perhaps you've setup Google Authenticator, Duo Mobile, or Microsoft Authenticator. These authenticators are available on the Google Play store and Apple App Stores.
Curious on how Azure Multi-Factor Authentication works I reached out to Chris Lee, Principal Consultant with Improving, and he kindly setup a demo environment for me to learn. The demo is setup with Azure AD Premium P2. If you are interested in following along, I recommend working with your Azure administrators to setup a demo environment for you. While you could also try the free trial, Chris recommended the demo environment.
Requirements
- This demo environment was automatically provisioned via Microsoft partnership
- Alternatively, Chris recommended setting up Enterprise Mobility + Security trial if you don't have an existing environment
- Create/Use an account with the domain of the demo environment
- Referenced as "domain user" throughout this article
- Install Microsoft Authenticator
- I installed it on my Android phone via the Google Play store
First-time Login as domain user
- https://account.activedirectory.windowsazure.com/
- I entered my password and clicked "Sign in"
- For these tests, I clicked "No"
- And I'm signed in… hmm MFA isn't setup
Setup MFA
The MFA settings allow you to manage account lockout, block/unblock users, and many other settings. Let's change the MFA to only allow Notification through mobile app. These settings affect all accounts within the Active Directory and B2B.
- https://portal.azure.com
- Login as an administrator
- Azure Active Directory > MFA
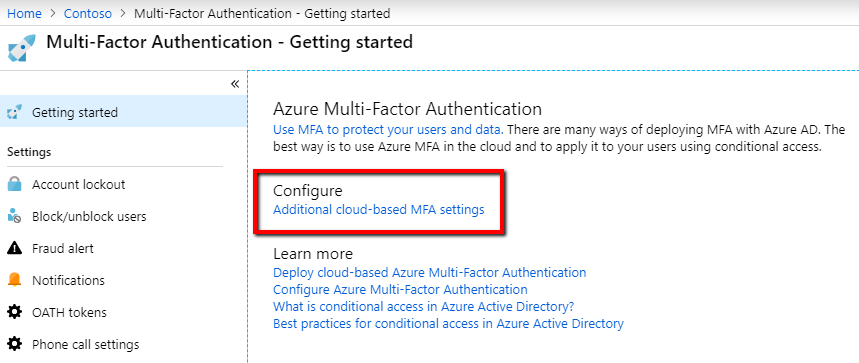
- Under Configure > click "Additional cloud-based MFA setting"
- Check "Notification through mobile app" and uncheck the other "Methods available to users" > Save
- Race condition to be aware of
- Domain user enters their username and password and clicks "Sign in"
- Administrator saves any of these changes
- Domain user clicks the "Next" button
- Expected behavior: Domain user sees the options that were just saved
- Actual behavior: Domain user see the original options
- Race condition to be aware of
- Check "Notification through mobile app" and uncheck the other "Methods available to users" > Save
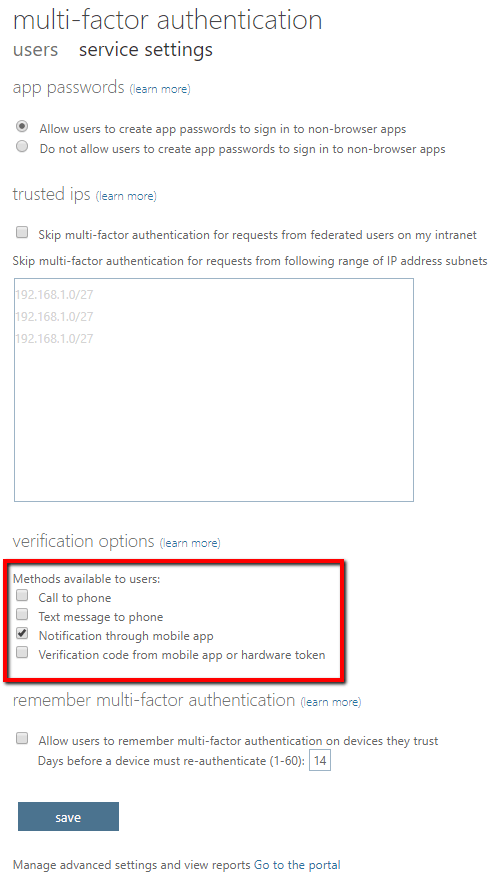
Ok, so MFA was already setup with "Text message to phone", "Notification through mobile app", and "Verification code from mobile app or hardware token" and now I've limited it to just "Notification through mobile app", but I still don't see any requirements for MFA. It's almost like MFA was not enabled for my account.
Enable MFA for an account
So yeah, my account needed MFA enabled. It's not obvious, but in the MFA page there are two tabs "users" and "service settings". By default, when you follow the previous steps you open into the "service settings" tab.
- Click the "users" tab
- Click the search icon (magnifying glass)
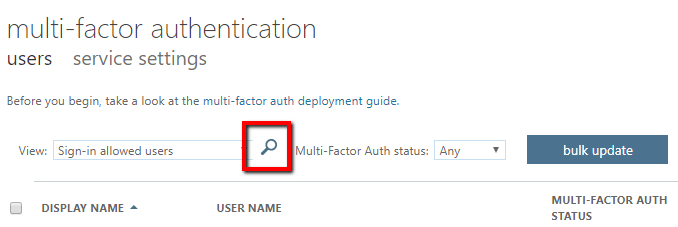
- Search for your domain user
- Yep, my account had MFA disabled, so under "quick steps," click the "Enable" link.
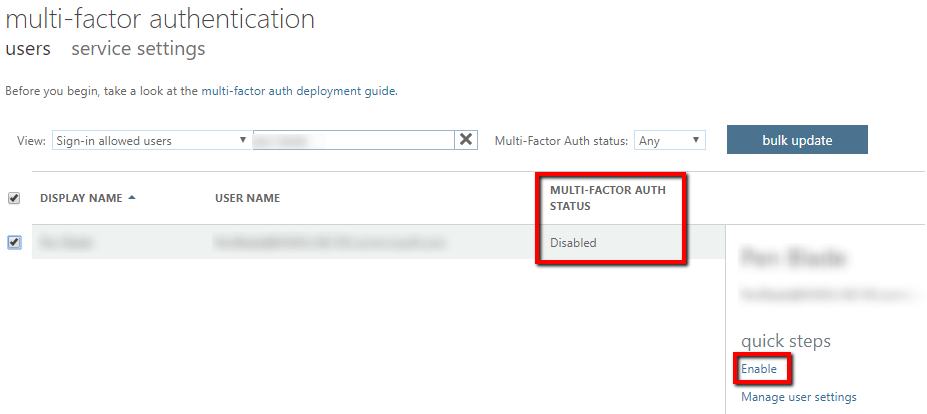
- The "About enabling multi-factor auth" modal opens > "enable multi-factor auth"
- Deployment guide link
- MFA Setup link
- Click "close" and verify that the MFA status for the domain account is now "Enabled"
- If you click "Manage user settings" you can perform the following tasks for the user
- Require selected users to provide contact methods again
- Delete all existing app passwords generated by the selected users
- Restore multi-factor authentication on all remembered devices
Second-time Login as domain user
- https://account.activedirectory.windowsazure.com/
- Login as the domain user with the email address and password like we did earlier
- Now we're prompted to enter more information > click "Next"
- "Use a different account" redirects back to the login page as expected
- "Learn more" opens a document to "Troubleshoot common two-factor verification problems"
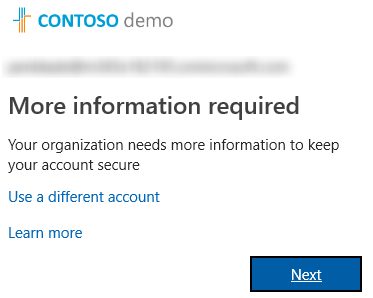
- Since we limited the options to just the Mobile app we only see that option
- "Manage your two-factor verification method settings" includes screenshots and instructions of the other methods
- "View video to know how to secure your account"
- Select "Receive notifications for verification" > Click "Set up" > Open the Microsoft Authenticator on your phone and scan in the bar code
- "Manage your two-factor verification method settings" includes screenshots and instructions
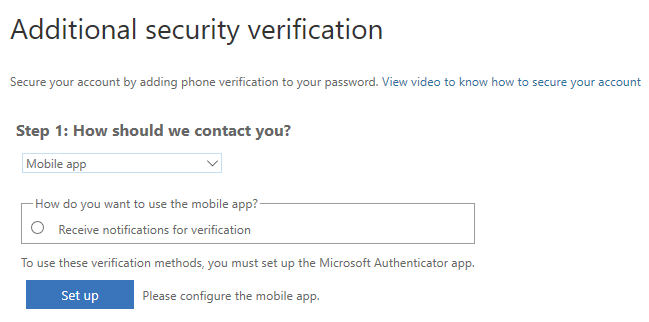
- "Manage your two-factor verification method settings" includes screenshots and instructions
- The next set of instructions ask if you want to store an app code, click "Done"
- Now I'm signed in, but do I have to do this every time? Nope, that's a one-time deal unless you reset your desired MFA method
Third times the charm
- https://account.activedirectory.windowsazure.com/
- Login as the domain user with the email address and password like we did earlier
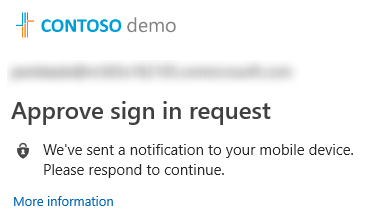
- Now we're prompted with a request to "Approve sign in request"
- On my phone I click the notification and click Approve on the request
- I'm signed in and ready to go
Self-Service
While an administrator can reset your MFA configuration so you can choose a different authentication method, it would be great to have the option to do it yourself.
- https://account.activedirectory.windowsazure.com/
- Sign in, approve, you're in
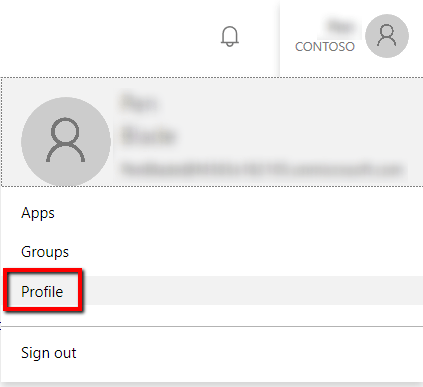
- Click your profile picture > Profile
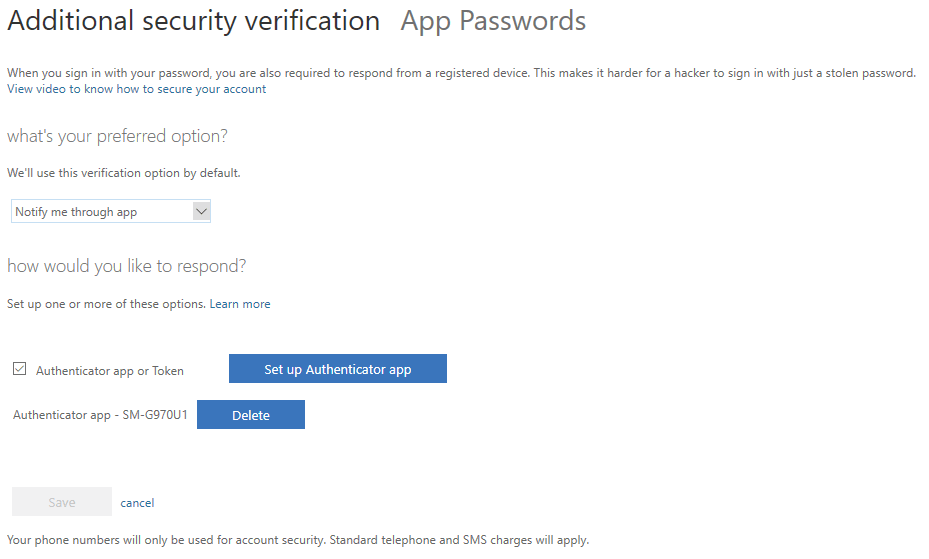
- Click "Additional security verification"
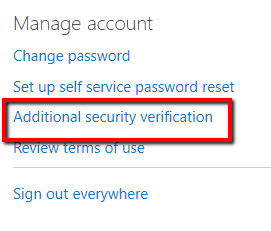
- Change your MFA options
- You're limited to what the administrator configured in MFA, but it's nice to reset the options you have control over and may save a call to the support desk.
Resources
- Azure Multi-Factor Authentication (MFA): From Configuration to Implementation - Azure Training
- What is conditional access? | Azure Active Directory
- Ensure all your users have strong passwords with Azure Active Directory Password - THR3047
- This video included some scary metrics.
- Configure Azure Multi-Factor Authentication settings
DogFoodCon 2019
DogFoodCon 2019 is October 3rd – 4th. Chris Lee and James Hopkins will be presenting [Office 365] Establishing the Baseline Security for Microsoft 365. Chris was well spoken, very informed, and he has a passion for security and helping others. He eagerly setup a demo environment for me to learn and test MFA at my convenience and can't thank him enough.
Chris Lee has been working with Microsoft 365 (M365) since its inception. He's been working with the Microsoft cloud from the beginning when it was called Business Productivity Online Suite (BPOS) which evolved into Office 365 which is a small part of M365. While most of his time has been devoted to Enterprise Mobility + Security he has plenty of experience with the other components as well.
Azure Multi-Factor Authentication is great start to setting up your baseline security. I've shown a small sample of the user experience and a how you can enable/disable the authentication methods. This session focuses solely on Microsoft security, so the target audience is anyone who has started or plan on using Microsoft cloud productivity solutions.
By attending their session you'll learn the following:
- Enterprise Mobility + Security E3 and Azure AD Premium P2
- Azure Multi-Factor Authentication
- Conditional Access
- Device Trust
- Password Practices
Special Thanks to Improving |
Conclusion
I have demonstrated the basic domain user experience when using Azure Multi-Factor Authentication and how to change which authentication methods are enabled. Next steps include learning Conditional Access, Device Trust, and Password Practices that you can learn more at DogFoodCon 2019.
What are your thoughts about MFA? Are you an Azure administrator just learning MFA? Are you a domain user taking a peek behind the curtains to learn how your IT handles MFA? What has been your experience with MFA as an administrator or domain user? Post your comments below and let's discuss.





